Achieving desired Requests per minute
If the Jmeter test is not able to send the expected Number of requests per minute then the following could the reasons:
REASONS WHY LESS REQUETS PER MINUTE ARE SENT VIA TEST
1. Number of request per minute will be lower if the server is not capable of handling it.
2. There's also going to be problems, especially with latency - even if you could send exactly 6 per second, they're going to be sent sequentially (that's just how packets get sent) and may not all hit in that second, plus processing time.
3. API-buffer overflow: Generally when performance metrics specific x per second, it is measured over a period of time. Your API may even have a buffer - so you could technically send 6 per second, but process 5 per second, with a buffer of 20, meaning it'd be fine for 20 seconds of traffic, as you'd have sent 120, which would take 120/5 = 24 seconds to process. But any more than that would overflow the buffer. Therefore, to just send exactly 6 in a second to test is insufficient.
CHECKS:
1. Check the JVM size in jmeter test.
Set HEAP=-Xms2560m -Xmx5120m
2. Run incremental Load like 50, 60, 80,100,110 monitor the JVM and decide how many injectors (separate jmeter instances) are required. Based on that split the load into multiple injectors and run simultaneously.
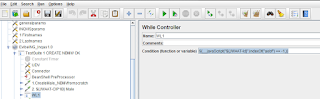
3. Try with Constant throughtput timer – to add a value for the RPM-requests per minute that are expected for a certain scenario.
If the Jmeter test is not able to send the expected Number of requests per minute then the following could the reasons:
REASONS WHY LESS REQUETS PER MINUTE ARE SENT VIA TEST
1. Number of request per minute will be lower if the server is not capable of handling it.
2. There's also going to be problems, especially with latency - even if you could send exactly 6 per second, they're going to be sent sequentially (that's just how packets get sent) and may not all hit in that second, plus processing time.
3. API-buffer overflow: Generally when performance metrics specific x per second, it is measured over a period of time. Your API may even have a buffer - so you could technically send 6 per second, but process 5 per second, with a buffer of 20, meaning it'd be fine for 20 seconds of traffic, as you'd have sent 120, which would take 120/5 = 24 seconds to process. But any more than that would overflow the buffer. Therefore, to just send exactly 6 in a second to test is insufficient.
CHECKS:
1. Check the JVM size in jmeter test.
Set HEAP=-Xms2560m -Xmx5120m
2. Run incremental Load like 50, 60, 80,100,110 monitor the JVM and decide how many injectors (separate jmeter instances) are required. Based on that split the load into multiple injectors and run simultaneously.
3. Try with Constant throughtput timer – to add a value for the RPM-requests per minute that are expected for a certain scenario.