Wednesday, April 6, 2016
Tuesday, April 5, 2016
Automated Regression test for Verification of XACML Policy responses (WSO2 carbon product platform)
XACML, shortened for extensible access control markup language, provides a flexible, fine-grained and scalable way of achieving policy-based access control. WSO2 carbon product platform provides a fine-grained access management solution with Policy Based Access Control (PBAC) based on XACML.
There are different mechanisms in use but they also have some drawbacks. Mechanisms like :
- User Centric Permission
- Role Based Access Control
- Attribute Based Access Control
have main Drawbacks like :
- non-scalability,
- coarse-grained permission and authorization logic being coupled with application logic which prevents flexibility.
Solution :
Policy-Based Access Control (PBAC).
This is emerging as a flexible and scalable solution for access management. XACML is a powerful way of achieving PBAC in a fine grained manner.
Steps to Setup:
Step1. Setup Identity Server. Configure MySQL database as WSO2 Identity Server’s data store.
Step2. Create XACML policies and XACML requests using tool.
Step3. Upload XACML policies in to Identity Server.
Step4. Configure script in test environment.
- Send call to specific Endpoint defined on IS. Use the soap envelop example:
POST data:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://org.apache.axis2/xsd">
<soapenv:Header/>
<soapenv:Body>
<xsd:getPolicy>
<!--Optional:-->
<xsd:policyId>Test-Scenario-4</xsd:policyId>
<!--Optional:-->
<xsd:isPDPPolicy>true</xsd:isPDPPolicy>
</xsd:getPolicy>
</soapenv:Body>
</soapenv:Envelope>
*****************
A parameterized policy example :
2.Single Permission, multiple groups, single rule
Parameters:
Policy id = $RAHULSPolicyId
Group name 1 = $RAHULSGroup1
Group name 2 = $RAHULSGroup2
Permission = $RAHULSPermission
Rule = $RAHULSRule
<Policy xmlns="urn:oasis:names:tc:xacml:3.0:core:schema:wd-17" PolicyId="$PolicyId" RuleCombiningAlgId="urn:oasis:names:tc:xacml:3.0:rule-combining-algorithm:deny-overrides" Version="1.0">
<Target>
<AnyOf>
<AllOf>
<Match MatchId="urn:oasis:names:tc:xacml:1.0:function:string-equal">
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">$RAHULSPolicyId</AttributeValue>
<AttributeDesignator AttributeId="urn:oasis:names:tc:xacml:1.0:resource:resource-id" Category="urn:oasis:names:tc:xacml:3.0:attribute-category:resource" DataType="http://www.w3.org/2001/XMLSchema#string" MustBePresent="true"></AttributeDesignator>
</Match>
</AllOf>
</AnyOf>
</Target>
<Rule Effect="Permit" RuleId="$Rule">
<Target>
<AnyOf>
<AllOf>
<Match MatchId="urn:oasis:names:tc:xacml:1.0:function:string-equal">
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">$RAHULSPermission</AttributeValue>
<AttributeDesignator AttributeId="urn:oasis:names:tc:xacml:1.0:action:action-id" Category="urn:oasis:names:tc:xacml:3.0:attribute-category:action" DataType="http://www.w3.org/2001/XMLSchema#string" MustBePresent="true"></AttributeDesignator>
</Match>
</AllOf>
</AnyOf>
</Target>
<Condition>
<Apply FunctionId="urn:oasis:names:tc:xacml:1.0:function:string-at-least-one-member-of">
<Apply FunctionId="urn:oasis:names:tc:xacml:1.0:function:string-bag">
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">$RAHULSGroup1</AttributeValue>
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">$RAHULSGroup2</AttributeValue>
</Apply>
<AttributeDesignator AttributeId="http://wso2.org/claims/role" Category="urn:oasis:names:tc:xacml:1.0:subject-category:access-subject" DataType="http://www.w3.org/2001/XMLSchema#string" MustBePresent="true"></AttributeDesignator>
</Apply>
</Condition>
</Rule>
</Policy>
**********************
- In this simple example, the policyId is checked and the response can be asserted for attribute values.
- Further when the call is sent to the Endpoint it will check the policy and revert with a response message. This response contains: policy and the attributes canbe verified. This scenario can be added to the regression test suite to ensure that all policy's are fine after a patch/update of Identity server/bug fix etc.,
- Parse the response on the attribute values and check if the policy is correct.
- similarly Soap message can be used for other attributes of the XACML Requests : Subject, Resource, Action.
Monday, March 14, 2016
Handling NTLM authentication in test automation - Single Sign ON
CASE:
There are many times situations where you have to switch between login accounts to execute a Test scenario. If the application is using SAML then it is not a problem. But what if the Application is using single sign on / NTLM authentication mechanism.
Understanding NTLM
NTLM is a suite of authentication and session security protocols used in various Microsoft network protocol implementations and supported by the NTLM Security Support Provider ("NTLMSSP"). Originally used for authentication and negotiation of secure DCE/RPC, NTLM is also used throughout Microsoft's systems as an integrated single sign-on mechanism. It is probably best recognized as part of the "Integrated Windows Authentication" stack for HTTP authentication; however, it is also used in Microsoft implementations of SMTP, POP3, IMAP (all part of Exchange), CIFS/SMB, Telnet, SIP, and possibly others.
The NTLM Security Support Provider provides authentication, integrity, and confidentiality services within the Window Security Support Provider Interface (SSPI) framework. SSPI specifies a core set of security functionality that is implemented by supporting providers; the NTLMSSP is such a provider. The SSPI specifies, and the NTLMSSP implements, the following core operations:
Solution:
HTTP sampler settings: JAVA
now java uses the single sign on user account with which you have logged into the laptop or test server. so while test execution or capturing the calls you might need to log into as a other user.
You can check if the application is using NTLM Authentication or not in Firefox (F12)/ Developer
: Network: Headers--> Request Headers of the login page call.
so to do so follow this :
open cmd and execute:
c:\RahulAgnihotri\apache-jmeter-2.13\bin>runas /user:ICS\ex000222002212 cmd
now in the new cmd execute:
c:\RahulAgnihotri\apache-jmeter-2.13\bin>jmeter.bat
Now you can proceed as this other user. Firefox will log in as a new ex000222002212
Start Task manager : Java process will be running with new user now: ex000222002212
There are many times situations where you have to switch between login accounts to execute a Test scenario. If the application is using SAML then it is not a problem. But what if the Application is using single sign on / NTLM authentication mechanism.
Understanding NTLM
NTLM is a suite of authentication and session security protocols used in various Microsoft network protocol implementations and supported by the NTLM Security Support Provider ("NTLMSSP"). Originally used for authentication and negotiation of secure DCE/RPC, NTLM is also used throughout Microsoft's systems as an integrated single sign-on mechanism. It is probably best recognized as part of the "Integrated Windows Authentication" stack for HTTP authentication; however, it is also used in Microsoft implementations of SMTP, POP3, IMAP (all part of Exchange), CIFS/SMB, Telnet, SIP, and possibly others.
The NTLM Security Support Provider provides authentication, integrity, and confidentiality services within the Window Security Support Provider Interface (SSPI) framework. SSPI specifies a core set of security functionality that is implemented by supporting providers; the NTLMSSP is such a provider. The SSPI specifies, and the NTLMSSP implements, the following core operations:
- Authentication -- NTLM provides a challenge-response authentication mechanism, in which clients are able to prove their identities without sending a password to the server.
- Signing -- The NTLMSSP provides a means of applying a digital "signature" to a message. This ensures that the signed message has not been modified (either accidentally or intentionally) and that that signing party has knowledge of a shared secret. NTLM implements a symmetric signature scheme (Message Authentication Code, or MAC); that is, a valid signature can only be generated and verified by parties that possess the common shared key.
- Sealing -- The NTLMSSP implements a symmetric-key encryption mechanism, which provides message confidentiality. In the case of NTLM, sealing also implies signing (a signed message is not necessarily sealed, but all sealed messages are signed).
Solution:
HTTP sampler settings: JAVA
now java uses the single sign on user account with which you have logged into the laptop or test server. so while test execution or capturing the calls you might need to log into as a other user.
You can check if the application is using NTLM Authentication or not in Firefox (F12)/ Developer
: Network: Headers--> Request Headers of the login page call.
so to do so follow this :
open cmd and execute:
c:\RahulAgnihotri\apache-jmeter-2.13\bin>runas /user:ICS\ex000222002212 cmd
now in the new cmd execute:
c:\RahulAgnihotri\apache-jmeter-2.13\bin>jmeter.bat
Now you can proceed as this other user. Firefox will log in as a new ex000222002212
Start Task manager : Java process will be running with new user now: ex000222002212
Tuesday, March 8, 2016
Friday, March 4, 2016
Thursday, March 3, 2016
Wednesday, February 17, 2016
WSO2 Identity server Test automation
This article describes and provides insights into creating Dynamic input based fully Automated test for user scenario testing for - WSO2 identity server authentication (involving authorization mechanisms like SAML2, OAUTH, JWT token)
Some common steps which can be 100% automated are as follows:
- A request for SAML2 authentication request. redirecting the user, using the returned URI, towards the Identity server.
- The returned value is an URI. It is expected from the web application to redirect the user towards the returned URI.
Re-direct based authentication using SAML2, SAML2 authentication request,JWT token verification - real time accessing of JWT token, API key.WSO2 Identity Server.
- user redirected the login-page of the Identity Server.
- The API Engine receives the authentication response on a callback endpoint. After parsing and validation of the response.
- API Gateway generated JWT token [complying RFC7519 and uses HMAC-256 digest and signature algorithm.] .
-- the JWT tokenis provided back to the Web application.
checking the JWT token from browser:Resources -->session Storage.
This is what you need to automate in real time each time the test executes.
JWT token can be decoded using the jwt.io for checking credentials.
Redirected command can also be retieved the same way in real time.
so each time a new jwt token is generated it is captured and pushed in with new call in the test script.
same way in callback saml response can be retieved and further channeled into calls.
Subscribe to:
Comments (Atom)
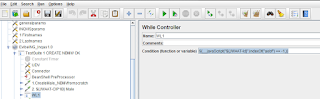
Json extractor and While loop
Waiting for a specific value in response of api request. using while loop. Add a While Loop. The api requets will be executed inside th...
-
Achieving desired Requests per minute If the Jmeter test is not able to send the expected Number of requests per minute then the followin...
-
# Starting nightly builds for regression testing in continous integration. Step1: Add a new Jenkins job. select : Freestyle project. ...
-
Sand box for collecting user stories. here in image below you see the user stories defined after meeting with team. Product owner can v...




















